一、背景
目前飞塔防火墙上IPv4拨号上网,现在想要通过IPv6访问内网设备。
设备型号:FortiGate 30E
设备名称:Firewall-SHA
设备版本:FortiOS v6.2.16 build1392 (GA)
公网口:wan
内网口:lan3
PS:需要登录到防火墙后台进行命令行操作,WEB界面IPv6功能极少
二、配置
1.公网口配置
这里的配置都是单独ipv6的配置,并不是清空你之前的配置,你之前的配置(例如IPv4的配置)不要去动!!!
具体内容:
config system interface
edit "wan"
config ipv6
set ip6-mode pppoe
set ip6-allowaccess ping
set dhcp6-prefix-delegation enable
set dhcp6-prefix-hint ::/60
set autoconf enable
end
next
end
---------------------------------------------------------------
详细步骤:
Firewall-SHA # config system interface
Firewall-SHA (interface) # edit wan
Firewall-SHA (wan) # config ipv6
Firewall-SHA (ipv6) # set ip6-mode pppoe
Firewall-SHA (ipv6) # set ip6-allowaccess ping
Firewall-SHA (ipv6) # set dhcp6-prefix-delegation enable
Firewall-SHA (ipv6) # set dhcp6-prefix-hint ::/60
Firewall-SHA (ipv6) # set autoconf enable
Firewall-SHA (ipv6) # end
Firewall-SHA (wan) # next
Firewall-SHA (interface) # end
Firewall-SHA # 2.内网口配置
这里的配置都是单独ipv6的配置,并不是清空你之前的配置,你之前的配置(例如IPv4的配置)不要去动!!!
具体内容:
config system interface
edit "lan3"
config ipv6
set ip6-mode delegated
set ip6-allowaccess ping
set ip6-send-adv enable
set ip6-manage-flag enable
set ip6-other-flag enable
set ip6-upstream-interface "wan"
set ip6-subnet ::2/64
config ip6-delegated-prefix-list
edit 1
set upstream-interface "wan"
set subnet ::/64
next
end
end
next
end
---------------------------------------------------------------
详细步骤:
Firewall-SHA # config system interface
Firewall-SHA (interface) # edit lan3
Firewall-SHA (lan3) # config ipv6
Firewall-SHA (ipv6) # set ip6-mode delegated
Firewall-SHA (ipv6) # set ip6-allowaccess ping
Firewall-SHA (ipv6) # set ip6-send-adv enable
Firewall-SHA (ipv6) # set ip6-manage-flag enable
Firewall-SHA (ipv6) # set ip6-upstream-interface wan
Firewall-SHA (ipv6) # set ip6-subnet ::2/64
Firewall-SHA (ipv6) # set ip6-other-flag enable
Firewall-SHA (ipv6) # config ip6-delegated-prefix-list
Firewall-SHA (ip6-delegated-pr~ist) # edit 1
new entry '1' added
Firewall-SHA (1) # set upstream-interface wan
Firewall-SHA (1) # set autonomous-flag enable
Firewall-SHA (1) # set onlink-flag enable
Firewall-SHA (1) # set subnet ::/64
Firewall-SHA (1) # next
Firewall-SHA (ip6-delegated-pr~ist) # end
Firewall-SHA (ipv6) # end
Firewall-SHA (lan3) # next
Firewall-SHA (interface) # end
Firewall-SHA # 3.配置防火墙IPv6安全策略
具体内容:
config firewall policy6
edit 1
set name "Default out"
set srcintf "lan3"
set dstintf "wan"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
set logtraffic all
next
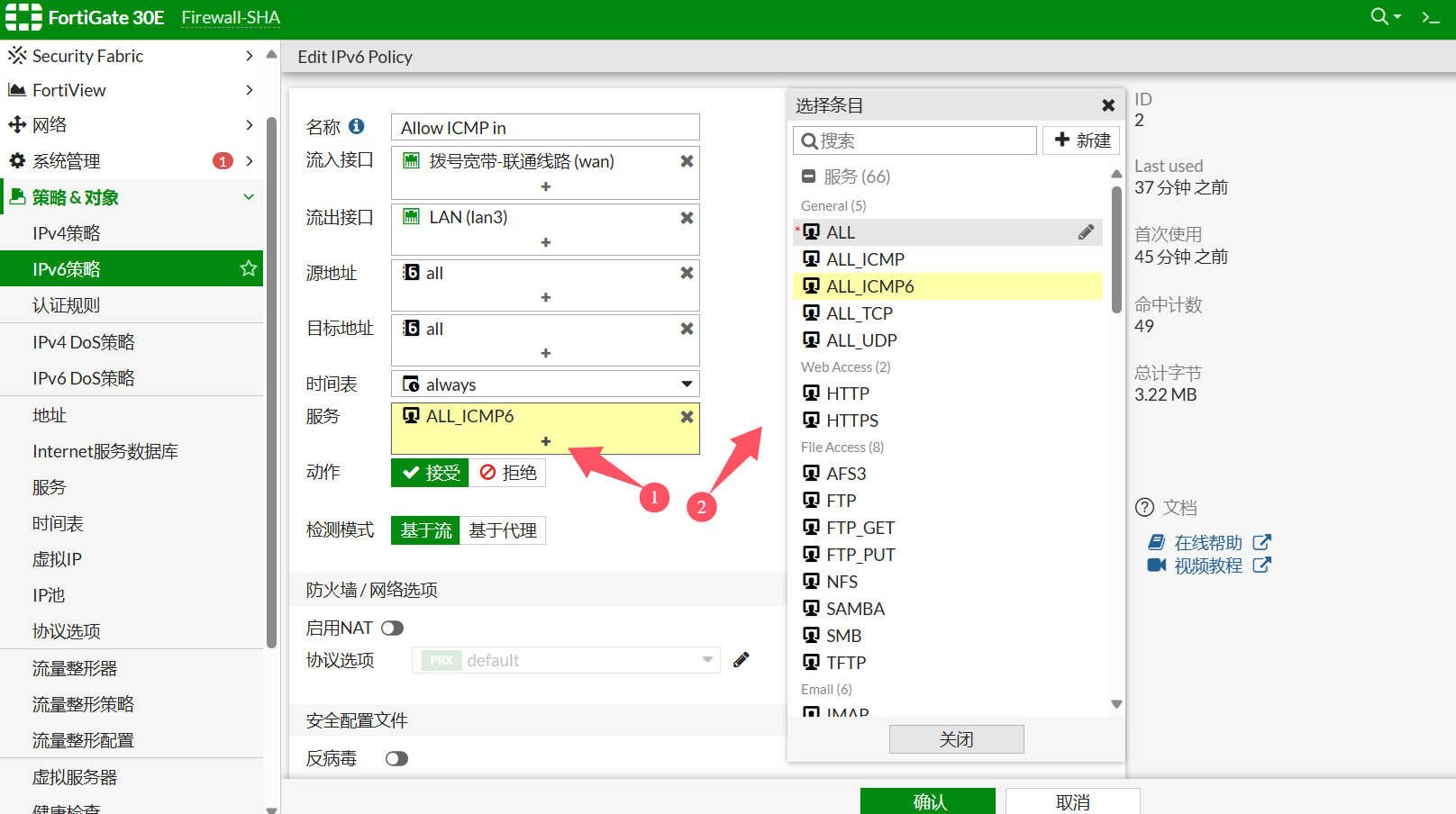
edit 2
set name "Allow ICMP in"
set srcintf "wan"
set dstintf "lan3"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL_ICMP6"
set logtraffic all
next
end
---------------------------------------------------------------
详细配置:
Firewall-SHA # config firewall policy6
Firewall-SHA (policy6) # edit 1
new entry '1' added
Firewall-SHA (1) # set name "Default out"
Firewall-SHA (1) # set srcintf lan3
Firewall-SHA (1) # set dstintf wan
Firewall-SHA (1) # set srcaddr all
Firewall-SHA (1) # set dstaddr all
Firewall-SHA (1) # set action accept
Firewall-SHA (1) # set schedule always
Firewall-SHA (1) # set service ALL
Firewall-SHA (1) # set logtraffic all
Firewall-SHA (1) # next
Firewall-SHA (policy6) #
Firewall-SHA (policy6) # edit 2
new entry '2' added
Firewall-SHA (2) # set name "Allow ICMP in"
Firewall-SHA (2) # set srcintf wan
Firewall-SHA (2) # set dstintf lan3
Firewall-SHA (2) # set srcaddr all
Firewall-SHA (2) # set dstaddr all
Firewall-SHA (2) # set action accept
Firewall-SHA (2) # set schedule always
Firewall-SHA (2) # set service ALL_ICMP6
Firewall-SHA (2) # set logtraffic all
Firewall-SHA (2) # next
Firewall-SHA (policy6) # end
Firewall-SHA #4.配置DCHPv6服务器
具体内容:
config system dhcp6 server
edit 1
set interface "lan3"
set ip-mode delegated
set upstream-interface "wan"
set dns-server1 2001:4860:4860::8888
set dns-server2 2001:4860:4860::8844
next
end
---------------------------------------------------------------
详细配置:
Firewall-SHA (server) # edit 1
new entry '1' added
Firewall-SHA (1) # set interface lan3
Firewall-SHA (1) # set ip-mode delegated
Firewall-SHA (1) # set upstream-interface wan
Firewall-SHA (1) # set dns-server1 2001:4860:4860::8888
Firewall-SHA (1) # set dns-server2 2001:4860:4860::8844
Firewall-SHA (1) # next
Firewall-SHA (server) # end
Firewall-SHA #三、验证
1.防火墙查看IPv6地址获取
Firewall-SHA # diag ipv6 address list
dev=7 devname=lan3 flag=P scope=0 prefix=64 addr=2408:****:****:****::2 preferred=4294967295 valid=4294967295 cstamp=25526955 tstamp=25526958
dev=16 devname=ppp1 flag= scope=0 prefix=64 addr=2408:****:****:****:****:****:****:682d preferred=172175 valid=258575 cstamp=25496145 tstamp=254961452.客户端查看IPv6地址获取
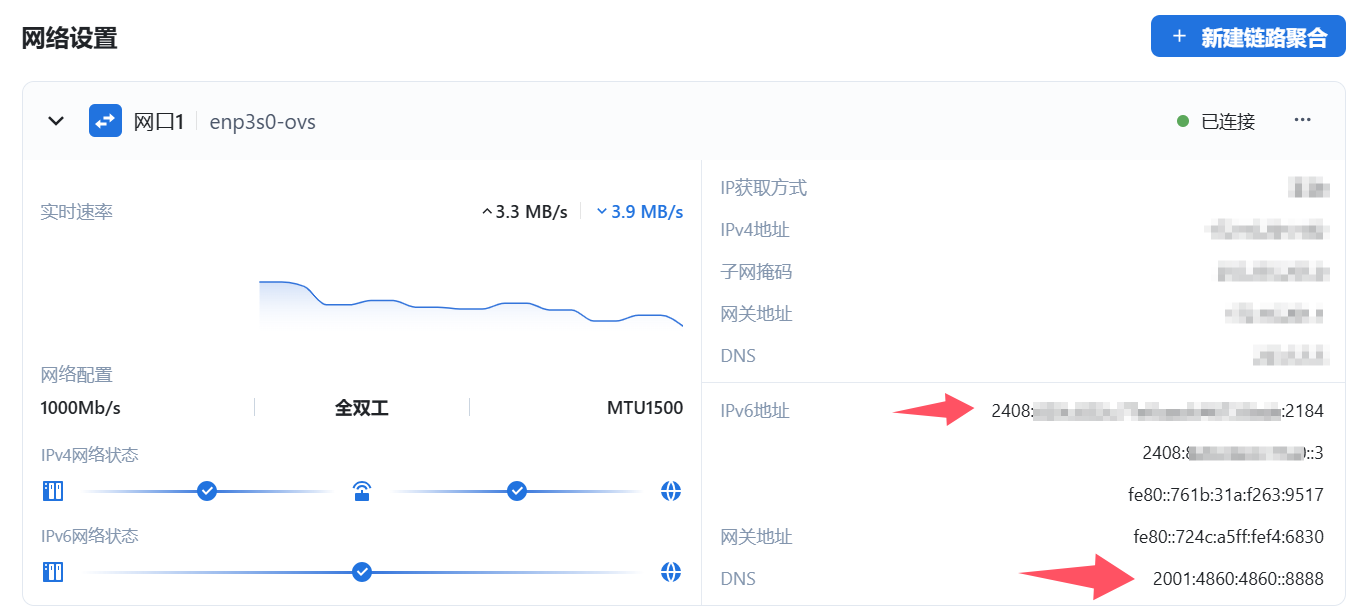
四、安全策略
通过修改防火墙IPv6的安全策略,实现公网v6访问内网客户端的对应服务
参考资料连接:分享文件 - 小飞机网盘【飞塔_FortiGate_50E-PPPOE获取IPV6地址.pdf】